
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Connect Okta to Identity Authentication
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-10-2020
2:21 AM
In this blog, we will explore how to establish trust between your Identity Authentication tenant and Okta as a corporate identity provider.
Once the connection between your Okta and the Identity Authentication is done, you can simply use it to connect it to several applications and environments.
Prerequisites
Log in to the Okta admin portal by going to https://login.okta.com/ and provide your credentials.
Click on the 'Use single sign on' - 'Add App' option.
Note: in Okta there is no predefined Identity Authentication application, you have to create and configure it manually.
For more information about configuration on the Okta side, refer to official Okta documentation: Create a SAML integration using AIW (Application Integration Wizard).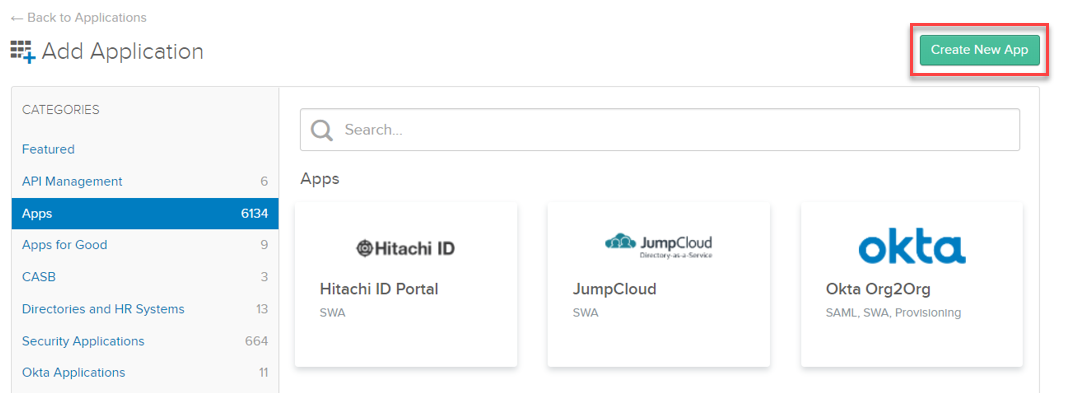
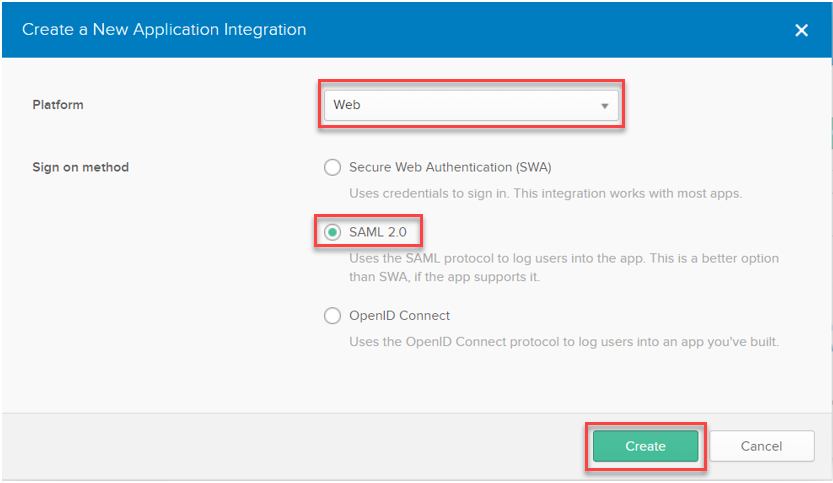
In the 'New Application Integration' tab choose Web as the platform, and SAML 2.0 as sign on method:
As the last part of the application creation, you can define a custom application name, logo, and visibility. Finally, click the Next button.

In this step, you have to fill in the SAML settings taken from Identity Authentication. Please pay special attention to all steps taken in this part.
To get URL value, follow steps:
After copy-pasting the URL, tick the 'Use this for Recipient URL and Destination URL' option.
*This is for SP-initiated SSO. If you'd like to use IdP-initiated SSO, construct the above 3 URLs like below:
https://<the current ACS endpoint URL>?sp=<sp_name>&index=<index_number>
Request the Entity ID of the service provider, and the index of the application's protected page from the tenant administrator of Identity Authentication.
The index is required.
On Okta it is possible to set both URLs (Allow this app to request other SSO URLs).
This has to be identical to the 'Name' value of your IAS tenant.
To get the URL, follow steps:
Copy value of the 'Name' field.
Note: Make sure the audience matches exactly as described in KBA 2693814 - Service Provider does not match the specified audience in the SAML2Assertion.
Default RelayState should be empty.
Leave further SAML settings default as well unless there are different requirements.
In Okta navigate to the 'Sign On' tab, then click the 'Identity Provider metadata' hyperlink to download the metadata in .xml format.
In this scenario, the Identity Authentication acts as a proxy to delegate the authentication to the corporate identity provider. For more information check our official SAP documentation: Configure Trust with Corporate Identity Provider.
Import the downloaded Okta metadata (from Step 3) into Identity Authentication:
Now almost all the required details are filled in:
Configure HTTP-POST Single Logout Endpoint URL with the same value set for the 'Name' value in IAS:
Save the configuration:
As a tenant administrator, you can specify a link that is sent as an extension in the SAML 2.0 Logout Response. The link can be used by the application to redirect the user after successfully logging out of the application when Identity Authentication acts as an identity provider proxy. See our official documentation: Service Provider Initiated Logout with Corporate Identity Providers.
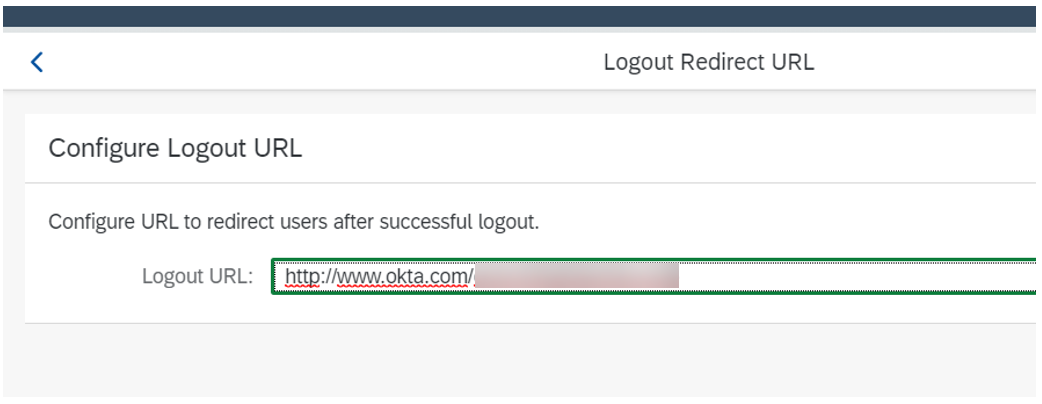
Navigate to the 'Trust' tab and choose the 'Logout Redirect URL' option. Define the desired URL where you want to redirect end-users after successful logout:
In the Administration Console of your IAS, navigate to 'Applications & Resources' then click on the 'Applications' tab and configure an application or choose an existing one.
Option A: Click on the 'Conditional Authentication' option on the 'Trust' tab of your application. Set your Okta as 'Default Identity Provider'.
For more information see our official documentation: Choose a Corporate Identity Provider as Default.
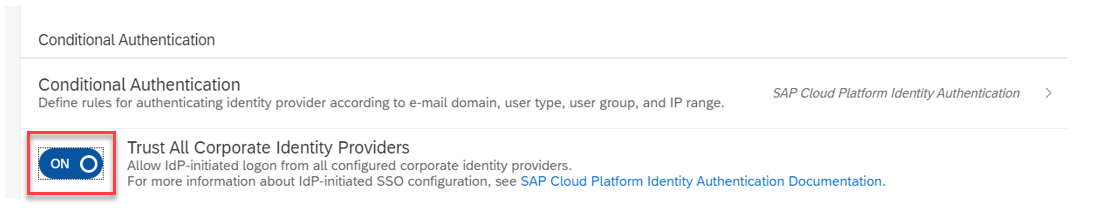
Option B: Set 'Trust all corporate Identity Providers' on. In this case, you should define Conditional Authentication to redirect users to Okta.
For more information see: Configure Conditional Authentication for an Application
After following the above steps, your application should use Okta as a corporate identity provider, and in this case, IAS is acting as a proxy.
Hint: If you are facing issues during configuration, you can download the Troubleshooting logs from your IAS tenant to self-investigate the root cause of the issue. See KBA 2942816 - How to export troubleshooting logs from Identity Authentication.
Also, we advise checking the IAS Guided Answers about the most common issues: KBA 2701851 - Identity Authentication (IAS) - Guided Answers.
Once the connection between your Okta and the Identity Authentication is done, you can simply use it to connect it to several applications and environments.
Prerequisites
- You have an active license for Identity Authentication.
- Manage Applications and Manage Corporate Identity Providers authorizations are assigned to you as Administrator in IAS.
- You have access to the Okta Admin portal.
Step 1: Log in to the Okta admin portal and create the SAML 2.0 application
Log in to the Okta admin portal by going to https://login.okta.com/ and provide your credentials.
Click on the 'Use single sign on' - 'Add App' option.
Note: in Okta there is no predefined Identity Authentication application, you have to create and configure it manually.
For more information about configuration on the Okta side, refer to official Okta documentation: Create a SAML integration using AIW (Application Integration Wizard).

In the 'New Application Integration' tab choose Web as the platform, and SAML 2.0 as sign on method:
As the last part of the application creation, you can define a custom application name, logo, and visibility. Finally, click the Next button.

Step 2: Create SAML Integration in Okta
In this step, you have to fill in the SAML settings taken from Identity Authentication. Please pay special attention to all steps taken in this part.
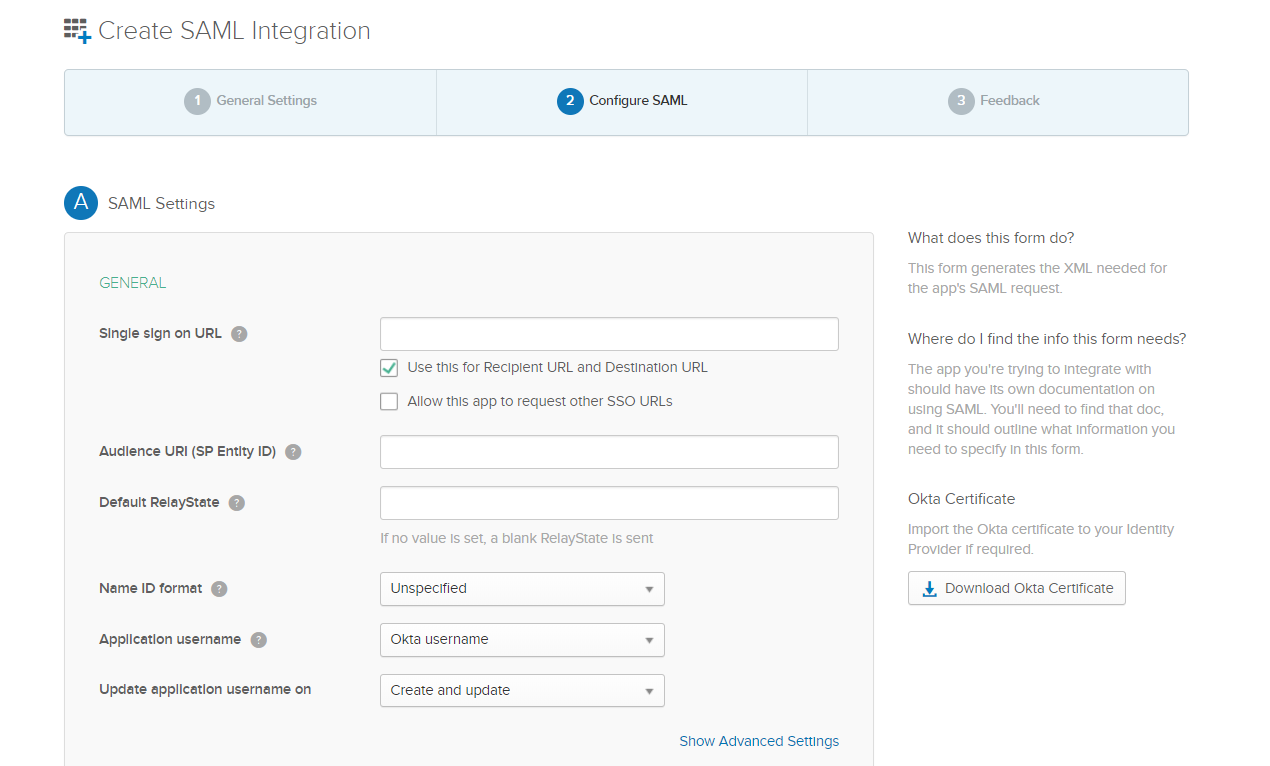
Single sign on URL:
To get URL value, follow steps:
- Open Identity Authentication (IAS) Administration Console: https://<tenantid>.accounts.ondemand.com/admin
- Navigate to the 'Tenant Settings' tile. Click on 'SAML2.0 Configuration'.
- Copy 'Assertion Consumer Service Endpoint' (ACS endpoint) URL.
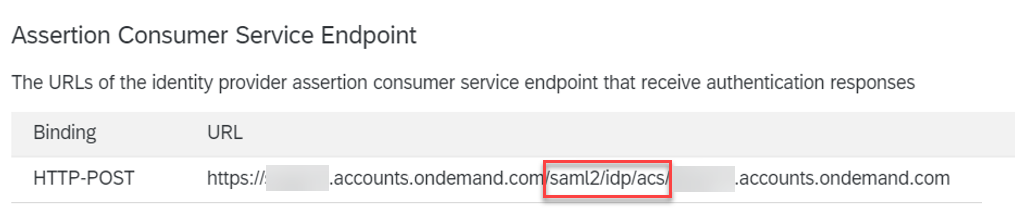
After copy-pasting the URL, tick the 'Use this for Recipient URL and Destination URL' option.
*This is for SP-initiated SSO. If you'd like to use IdP-initiated SSO, construct the above 3 URLs like below:
https://<the current ACS endpoint URL>?sp=<sp_name>&index=<index_number>
Request the Entity ID of the service provider, and the index of the application's protected page from the tenant administrator of Identity Authentication.
The index is required.
On Okta it is possible to set both URLs (Allow this app to request other SSO URLs).
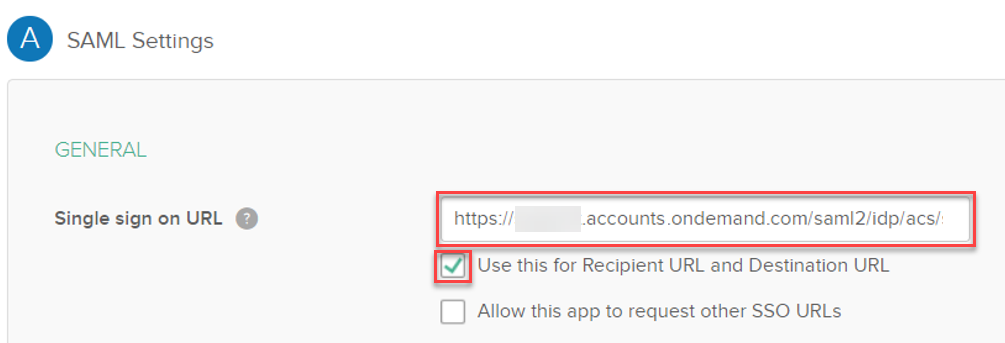
Audience URI (SP Entity ID):
This has to be identical to the 'Name' value of your IAS tenant.
To get the URL, follow steps:
- Open IAS Administration Console: https://<tenantid>.accounts.ondemand.com/admin
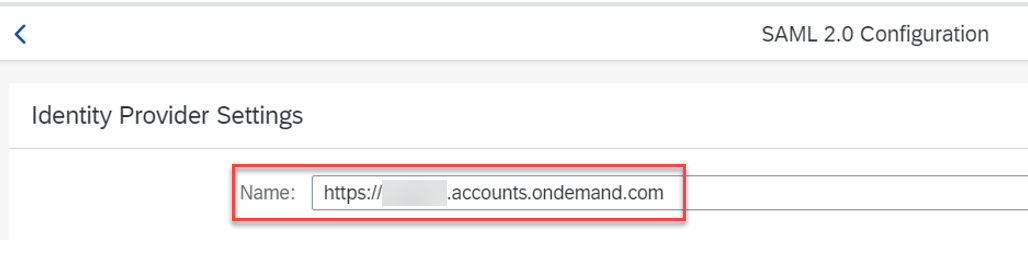
- Navigate to the 'Tenant Settings' tile. Click on 'SAML2.0 Configuration'.
Copy value of the 'Name' field.
Note: Make sure the audience matches exactly as described in KBA 2693814 - Service Provider does not match the specified audience in the SAML2Assertion.
Default RelayState should be empty.
Leave further SAML settings default as well unless there are different requirements.
Step 3: Download Identity Provider metadata file from Okta
In Okta navigate to the 'Sign On' tab, then click the 'Identity Provider metadata' hyperlink to download the metadata in .xml format.
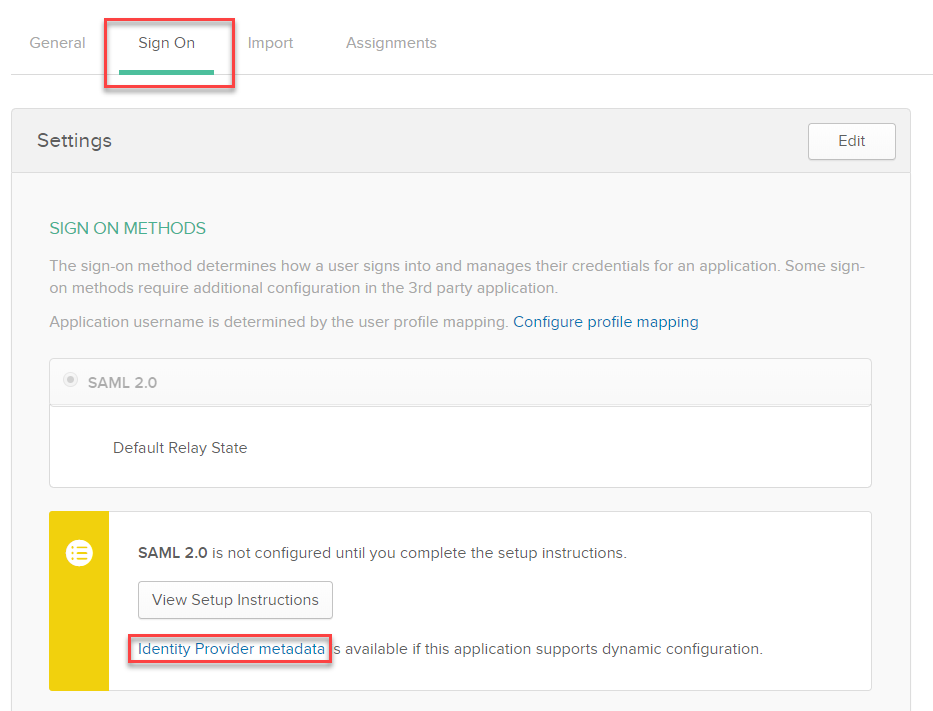
Step 4: Configure trust in the Identity Authentication tenant
In this scenario, the Identity Authentication acts as a proxy to delegate the authentication to the corporate identity provider. For more information check our official SAP documentation: Configure Trust with Corporate Identity Provider.
To use Identity Authentication as a proxy to delegate authentication to an external corporate identity provider you have to configure trust with that corporate identity provider.
To configure trust with the corporate identity provider, follow the procedures below:
Import the downloaded Okta metadata (from Step 3) into Identity Authentication:
- Open IAS Administration Console: https://<tenantid>.accounts.ondemand.com/admin
- Navigate to 'Corporate Identity Providers' in the submenu of 'Identity Providers'.
- Add Identity Provider with a custom name.
- Choose SAML 2.0 Configuration and import metadata:
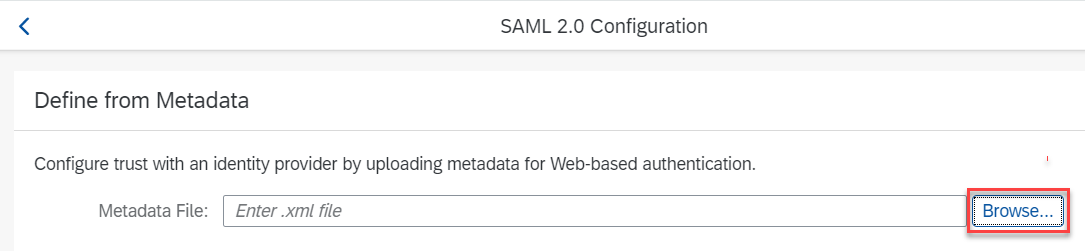
Now almost all the required details are filled in:
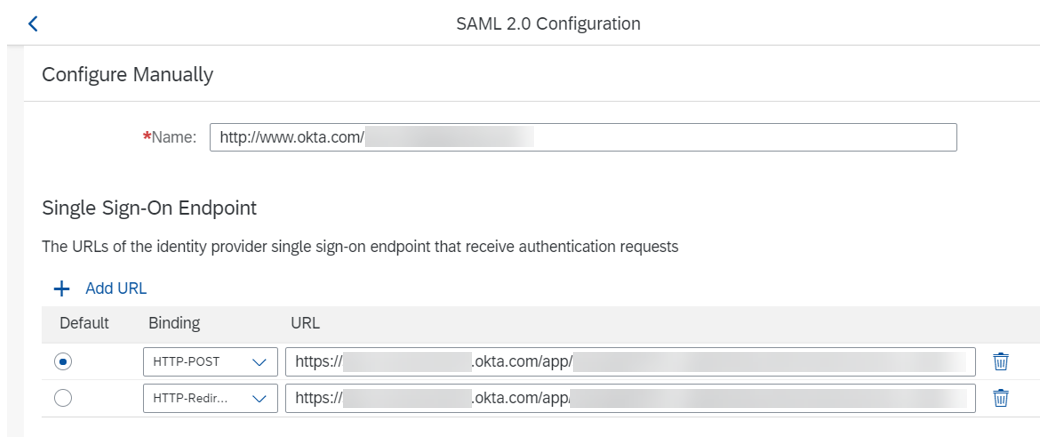
Configure HTTP-POST Single Logout Endpoint URL with the same value set for the 'Name' value in IAS:
Save the configuration:
As a tenant administrator, you can specify a link that is sent as an extension in the SAML 2.0 Logout Response. The link can be used by the application to redirect the user after successfully logging out of the application when Identity Authentication acts as an identity provider proxy. See our official documentation: Service Provider Initiated Logout with Corporate Identity Providers.
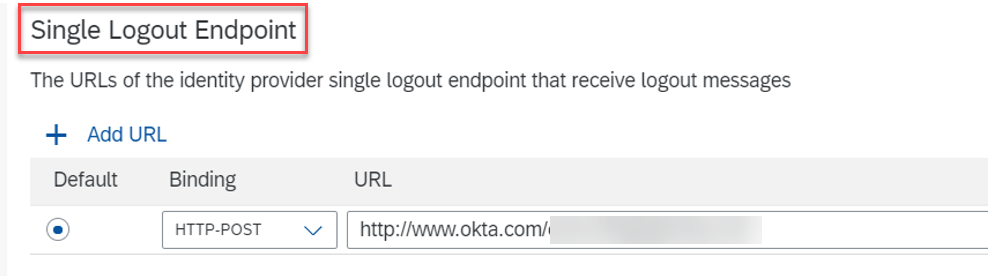
Navigate to the 'Trust' tab and choose the 'Logout Redirect URL' option. Define the desired URL where you want to redirect end-users after successful logout:
Step 5: Connect your application to use Okta as the identity provider
In the Administration Console of your IAS, navigate to 'Applications & Resources' then click on the 'Applications' tab and configure an application or choose an existing one.
Option A: Click on the 'Conditional Authentication' option on the 'Trust' tab of your application. Set your Okta as 'Default Identity Provider'.

For more information see our official documentation: Choose a Corporate Identity Provider as Default.
Option B: Set 'Trust all corporate Identity Providers' on. In this case, you should define Conditional Authentication to redirect users to Okta.
For more information see: Configure Conditional Authentication for an Application
Summary
After following the above steps, your application should use Okta as a corporate identity provider, and in this case, IAS is acting as a proxy.
Hint: If you are facing issues during configuration, you can download the Troubleshooting logs from your IAS tenant to self-investigate the root cause of the issue. See KBA 2942816 - How to export troubleshooting logs from Identity Authentication.
Also, we advise checking the IAS Guided Answers about the most common issues: KBA 2701851 - Identity Authentication (IAS) - Guided Answers.
- SAP Managed Tags:
- SAP BTP Security,
- SAP Cloud Identity Services,
- Security
Labels:
35 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
105 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
69 -
Expert
1 -
Expert Insights
177 -
Expert Insights
331 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,575 -
Product Updates
376 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,872 -
Technology Updates
463 -
Workload Fluctuations
1
Related Content
- Embedding Business Context with the SAP HANA Cloud, Vector Engine in Technology Blogs by SAP
- SAP BTP FAQs - Part 2 (Application Development, Programming Models and Multitenancy) in Technology Blogs by SAP
- Configuring SAP CI/CD pipeline for Deploying ReactJS application in Cloud Foundry in Technology Blogs by Members
- Cache OAuth token using Cache policies in SAP APIM in Technology Q&A
- SAP CAP Java hybrid development in BAS in Technology Q&A
Top kudoed authors
| User | Count |
|---|---|
| 16 | |
| 12 | |
| 9 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 5 |